Faytech Freestyle: Interactive Digital Whiteboard Solution
The faytech Freestyle interactive whiteboard will transform the way you present and share information! This whiteboard features the following:
- 4K Camera
- High-Quality Display
- Advanced Touch Technology
- Durability and Visual Comfort
- Versatile Connectivity Options


$5,764
$4,475
$3,723
Invest in Digital Smart Interactive Whiteboards Technology for Educational & Commercial Applications
Discover Faytech’s smart touch screen whiteboard technology solutions, designed to revolutionize education and commercial applications by facilitating interactive learning and collaborative work environments. Transform your presentations today—explore our range of digital whiteboards to see how we transform interactive experiences.

Specifications
- 4K (3840x2160px) Quad-HD Display
- AmLogic A311D2 Mainboard
- 20-Point IR Touch
- VESA Mounting Pattern – Wall mount of use included stand
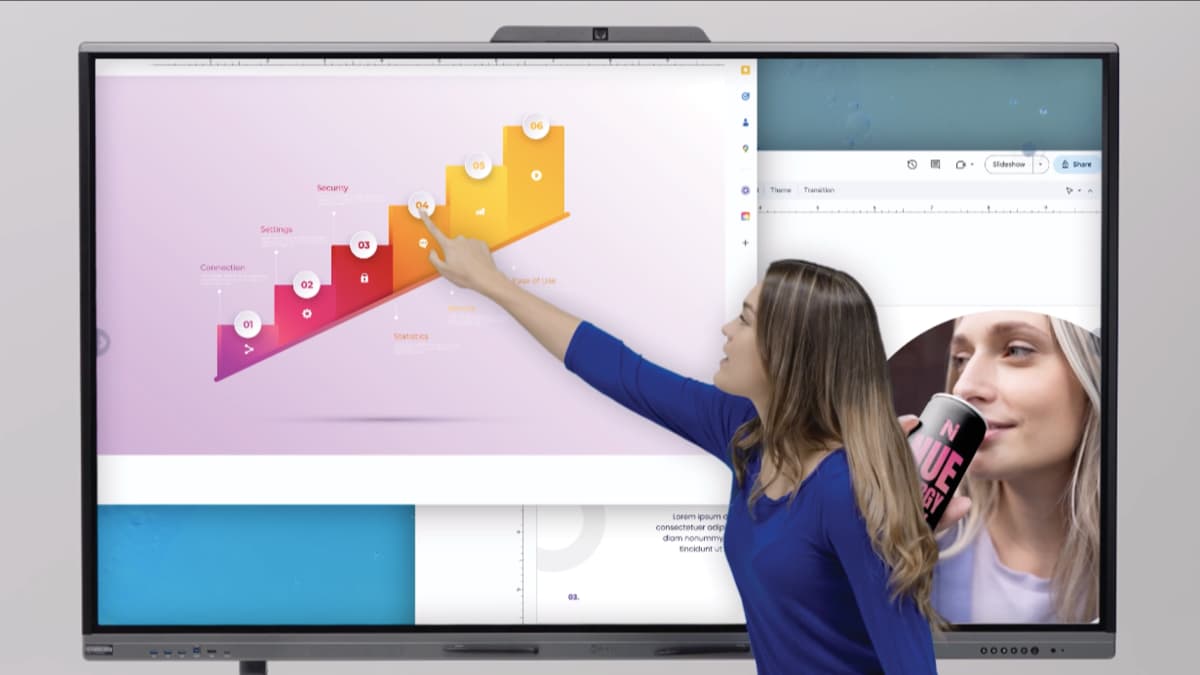
Smart Usability
- Included SmartPen can be used as a stylus or presentation remote
- Gesture-Based Functions allow you to use your hand as an eraser
- Built-in screen recording allows you to capture your whiteboard session
Google Play Store Certified
- Browse over 2.6 Million apps on the Google Play Store
- Sign-in with your Google Account to sync and manage your device settings and apps
- Download and install the latest apps from your favorite developers
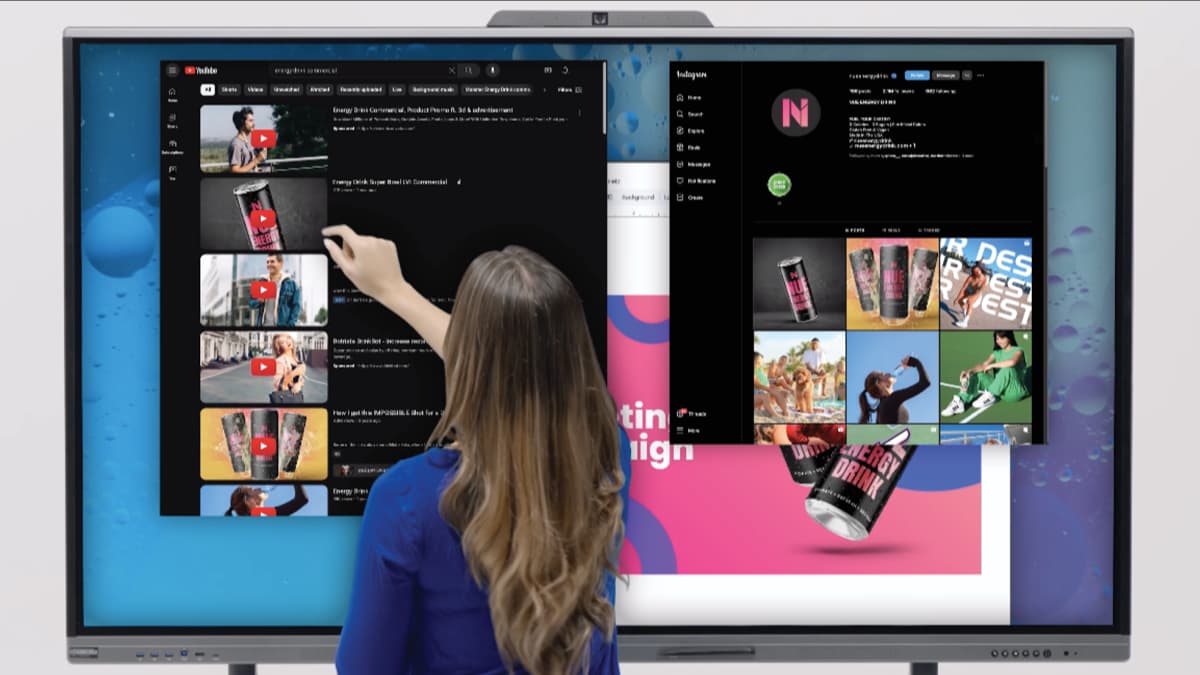
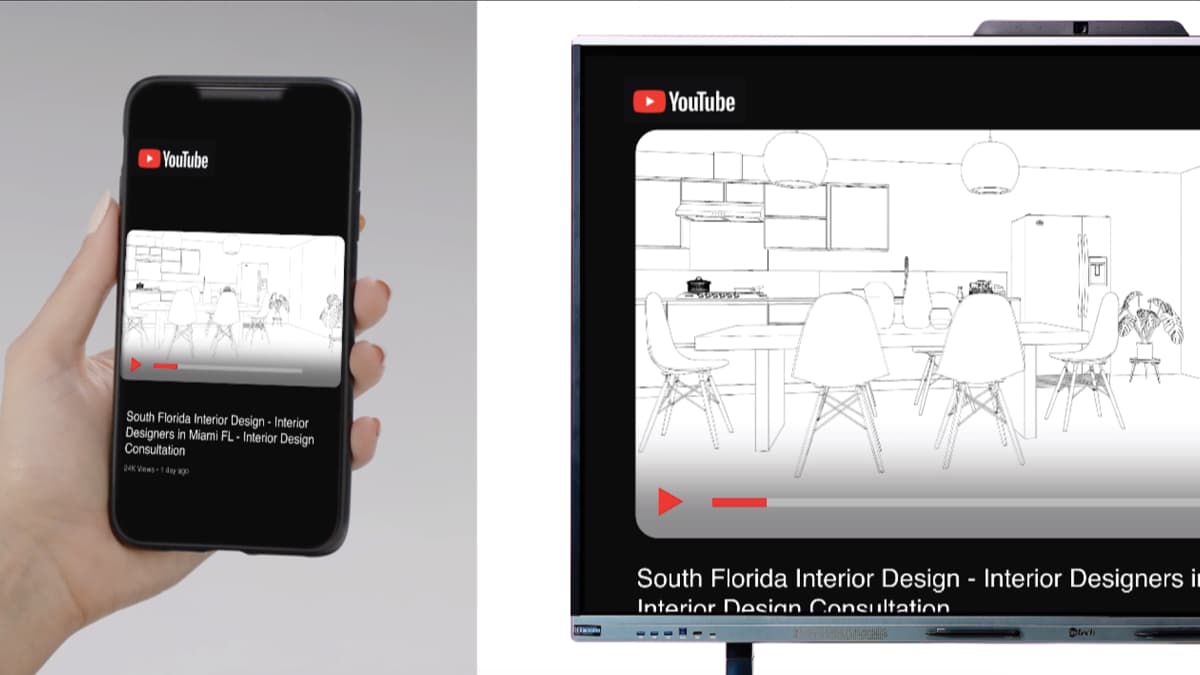
Effortless Screen Sharing
- Connect your mobile device with the Smartboard using a QR code (Airplay for Apple Devices or MiraCast for Android Devices)
- Wirelessly cast photos, videos, music, documents and files to the Smartboard

Ultimate Customization
- Android 11 (Red Velvet Cake) – Upgradeable to Android 13
- External Inputs – Use your Smartboard as a monitor (HDMI, DP, USB-C)

Built for Business and Education
- Google EDLA certified for security and privacy
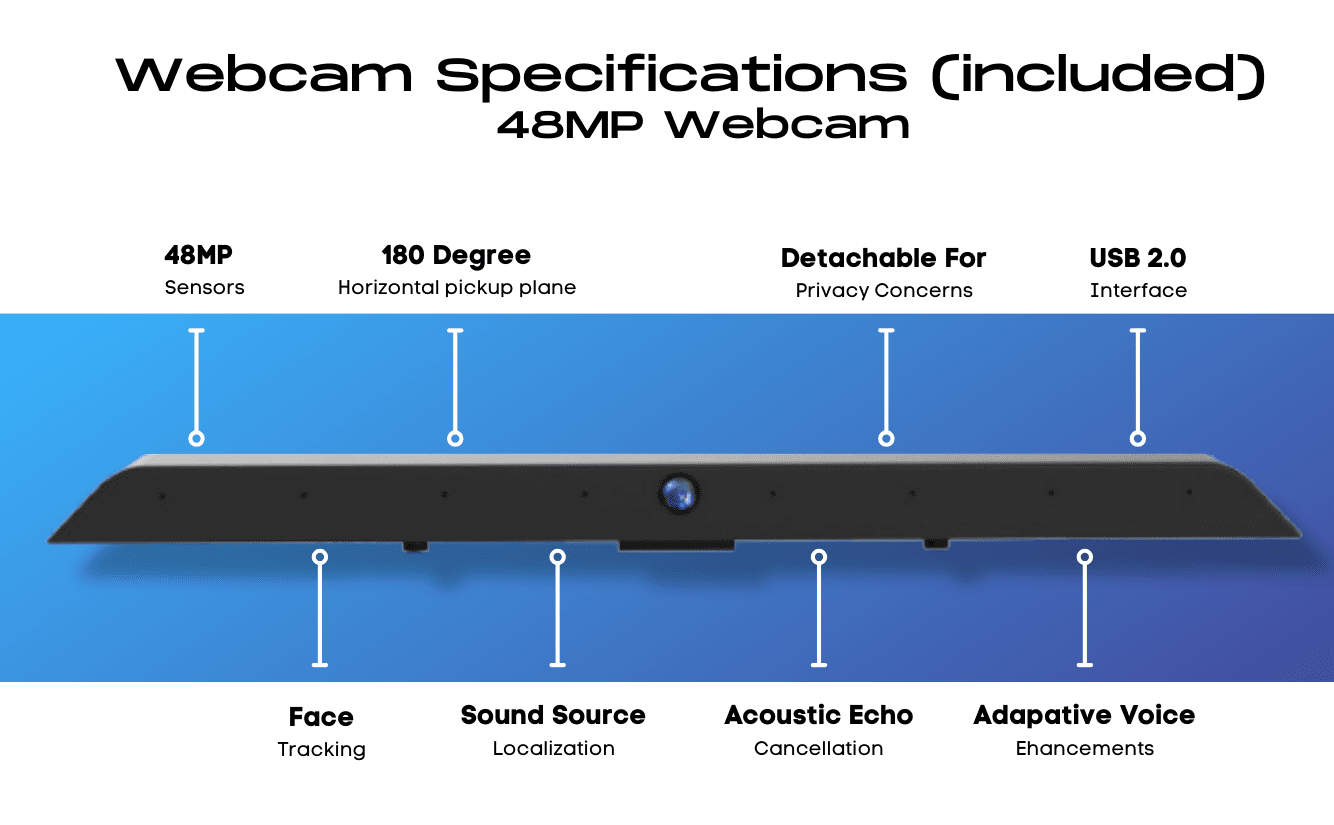
- Included removable 48MP camera with multi-array microphones
- Microsoft Teams and Google Workspace Compatible
Interactive Whiteboards for Meetings & Educational Experiences
- IP65 Design
- High-Brightness LCD
- Anti-Vandal IK08 Glass
- Ultra-Bright LED Lighting Strip
- Recessed or Surface Mount



More Information
What are Interactive Whiteboards?
Interactive whiteboards, also called smart boards or interactive digital whiteboards, have changed how we share and present information. These advanced multimedia presentation boards mix the traditional whiteboard with touchscreen technology. This makes it easy for users to interact directly with the content shown. They work great as collaborative tools that help keep everyone engaged during meetings, presentations, and classroom activities.
These devices allow users to blend different media types, like videos, images, and documents. This combination creates an exciting learning environment that boosts user interaction. Features like multi-touch support and gesture recognition make it easy for everyone to share ideas and work together.
Definition and Key Features
An interactive whiteboard is a large display connected to a computer that recognizes touch from fingers or styluses. It aims to enhance educational technology by providing visual learning tools that meet different teaching needs.
Key features include:
- Touchscreen Technology: Users can control content directly on the board.
- Engagement Tools: Helps in active participation through polls or quizzes.
- Multimedia Integration: Supports various formats for more dynamic presentations.
- Collaboration Capabilities: Multiple users can interact at once.
These features make interactive whiteboards essential tools in classrooms and business settings.
How Interactive Digital Whiteboards Work
Interactive whiteboards use advanced display technology for user interaction. When you touch the surface, sensors in the board detect the action. This lets you move objects on-screen or write notes during discussions.
Content sharing is also straightforward. Teachers or presenters can wirelessly project their screens onto the board from laptops or tablets. This feature simplifies communication and encourages teamwork among members who might be contributing from different locations using compatible software.
The Evolution of Interactive SMART Whiteboards
Interactive whiteboards have evolved significantly over the years due to advancements in display technology. They started as basic projection systems with limited interactivity but have turned into powerful smart technologies today.
As education moved toward more engaging teaching methods, often called “digital classrooms,” interactive electronic whiteboards became vital. Current models offer high-definition displays and connectivity options like Wi-Fi, making them key tools across various industries including education, business training, healthcare seminars, and retail customer interactions.
| Feature | Traditional Whiteboard | Interactive Whiteboard |
|---|---|---|
| User Interaction | None | Touch-sensitive interface |
| Content Sharing | Manual projection | Wireless screen mirroring |
| Media Compatibility | Limited | Supports videos/images/documents |
| Collaboration | One-way communication | Multi-user collaboration |
This table shows how we’ve moved from simple teaching aids to fully integrated solutions that promote interactivity in professional environments while enhancing overall productivity.
Faytech Interactive Whiteboards: A Superior Alternative
Why Choose Faytech Interactive Whiteboards?
Faytech’s interactive whiteboards are made for today’s workspaces and schools. An interactive whiteboard changes how teams work together, making it easier to get everyone involved during meetings or classes. These devices act as a smart board interactive whiteboard, using advanced display technology that is easy to touch and use.
Key features include:
- Touch Screen Board: Users can touch the screen to interact with what is shown, which helps everyone collaborate smoothly.
- Collaborative Whiteboard Functions: Several people can write or draw at the same time, which improves discussions and idea sharing.
- Digital Collaboration Tools: Built-in software allows users to edit and share ideas in real-time.
These boards focus on educational technology, enhancing engagement and creating a lively learning space. They work well in classrooms that want to include visual learning tools, ensuring all students join in actively.
Faytech’s Advantages
Faytech’s interactive whiteboards offer several important benefits that improve user interaction and presentation effectiveness:
- Multimedia Presentation Board Capabilities: You can add videos, images, and web pages to make presentations exciting.
- Engagement Tools: Features like polls and quizzes help teachers check student understanding quickly.
- User Interaction Enhancements: Touch gestures let users easily move through materials without needing extra tools.
- Visual Learning Tools Integration: High-resolution screens provide clear visuals that support instructional technology effectively.
These benefits make our interactive whiteboards perfect for corporate training or classrooms where active participation is key for keeping knowledge.
Comparing Faytech to Alternatives (e.g., Vibe Board)
When you look at Faytech compared to alternatives like the Vibe Board, a few things stand out:
- Both offer AV solutions for distance learning, but Faytech works better across many platforms, boosting usability in corporate training tools.
- For e-learning solutions, our boards allow customization that fits different organizational needs—something many competitors don’t provide.
| Feature | Faytech Interactive Whiteboard | Vibe Board |
|---|---|---|
| Compatibility | Extensive | Limited |
| User Interface | Highly customizable | Standardized |
| Multimedia Support | Yes | Basic |
| Ideal For | Corporate & Education | Primarily Educational |
This comparison shows why businesses looking for good collaborative tools should choose faytech North America’s innovative approach instead of standard options available on the market today.
Faytech’s Commitment to Sustainability
At faytech North America, we know sustainability matters in education technology. Our commitment goes beyond high-quality products; we also care about eco-friendly practices:
- We use sustainable materials whenever possible when creating our interactive devices.
- Our products are built to last longer, reducing waste from frequent replacements that often happen with lower-quality options.
By picking faytech’s eco-friendly products for classrooms and offices, organizations invest in great technology while also supporting environmental efforts in their communities.
Benefits and Applications of Interactive Whiteboards
Benefits for Businesses
Enhanced Collaboration and Productivity
Interactive whiteboards are great tools for businesses. They help teams work better together. With features like multi-touch support, everyone can join in during meetings. This makes brainstorming fun and interactive. Teams can share ideas visually on a big screen, which encourages more people to speak up.
Using touchscreen technology makes it easy to show videos or diagrams while talking. This helps explain tricky topics clearly. Overall, businesses that use these tools see better teamwork and more productive meetings.
Cost-Effective Solutions for Meetings
In busy workplaces, saving time and money is key. Interactive whiteboards are cost-effective solutions for meetings because they combine many functions into one device. No need for separate projectors or screens anymore.
This setup saves on printing costs, too. By having everything in one place, it cuts down on the hassle of setting up equipment. Many companies find that buying an interactive display pays off over time by saving them money and effort.
Applications Across Industries
Education
In schools and classrooms, interactive whiteboards make learning more exciting. Teachers can create digital lessons that keep students interested. These tools support different learning styles with e-learning solutions that include videos and animations.
Students get to touch the screen, making them part of the lesson. This approach leads to a fun and engaging atmosphere where students are eager to participate.
Corporate
In the corporate world, these boards shine during training sessions or team meetings where feedback is important. Real-time document annotation helps everyone understand what’s being discussed clearly. Teams can visualize data together, leading to faster decision-making.
Using digital collaboration features on these boards also improves communication among colleagues. This way, companies ensure everyone is on the same page during discussions.
Healthcare
Healthcare professionals benefit a lot from interactive displays during staff training or when educating patients about their conditions. Visual aids simplify tough health information, making it easier to understand.
Remote learning solutions also play a role in healthcare education. These options let medical workers keep learning no matter where they are located.
Retail
Retail stores increasingly use interactive technology to connect with customers. Touchscreen displays allow shoppers to explore products easily. This interaction not only improves customer experience but also boosts sales conversions because customers enjoy engaging with items before buying them.
Overall, interactive whiteboards provide significant benefits across various sectors—from improving teamwork in offices to enhancing student experiences in classrooms and creating memorable shopping experiences in stores.
Selecting and Utilizing Faytech Digital Whiteboards
Key Features to Consider
When looking for an interactive whiteboard, you should focus on features that boost its usefulness. An interactive whiteboard can really help in schools or businesses. Here are the main features to think about:
Multi-Touch and Gesture Support
A board with multi-touch support lets many people use it at the same time. This is super helpful for teamwork. An interactive digital whiteboard can make user interaction fun and engaging during lessons or brainstorming sessions. With great gesture recognition, users can move through content easily, encouraging more participation.
Screen Size and Resolution
The size of the screen is important for how well everyone sees the information. A bigger screen helps everyone in the room see better, while high-resolution screens ensure clear visuals for learning tools like images or graphs. Choosing a multimedia presentation board that has the right balance between size and clarity will keep everyone involved without straining their eyes.
Compatibility and Connectivity
Make sure your touch screen board connects easily with your current AV solutions. This matters a lot for corporate training tools and remote learning solutions. Look for boards with multiple connectivity options like HDMI, USB ports, Wi-Fi, and Bluetooth so you can connect to laptops or mobile devices without hassle.
Durability and Maintenance
You want an interactive electronic whiteboard that lasts. Since these boards get used a lot, they need to be strong and reliable over time. Regular upkeep is key, but picking a model designed as a versatile workstation helps reduce maintenance needs by using materials that resist damage from frequent use.
Choosing the Right Interactive Whiteboard
Picking the right interactive whiteboard means thinking about what fits best in your environment, whether that’s schools or corporate digital classrooms.
Factors to Consider
Consider these important factors:
- Usage: Think about if you will mostly teach concepts visually (like in schools) or hold meetings (like in business).
- User interface: Check how easy it is to use based on users’ tech skills.
- Integration: See if it works well with other instructional technology already used in your organization.
Pricing and Configurations
Understanding how pricing works helps you find good e-learning solutions that fit your budget while still having quality features needed for effective communication in any workspace.
Using Your Faytech Interactive Whiteboard
After you select your Faytech interactive whiteboard, knowing how to use it well makes the most of this investment for distance learning or online collaboration with teams far apart.
Setup and Installation Guide
Here’s how to set it up:
- Place the board at eye level.
- Connect power sources and cables based on your choices.
- Install recommended software from Faytech North America for smooth setup.
- Test everything before starting so you can fix issues right away!
Doing this will help things run smoothly during content-sharing sessions in meeting spaces where everyone can interact easily.
Tips for Optimal Use
To get the best out of your touch screen board:
- Encourage brainstorming sessions using built-in tools that allow annotations—this sparks creativity!
- Use visual aids often in lectures or presentations to keep attention while explaining complex ideas simply!
By following these strategies along with understanding key features mentioned earlier, using innovative tech can lead to better productivity overall!
Faytech: Your Partner for Interactive Whiteboard Solutions
Why Choose Faytech?
Faytech North America offers great interactive whiteboards that boost educational technology. These tools support digital collaboration and are perfect for modern workspaces. Our collaborative whiteboards help businesses looking for smart technology and advanced AV solutions.
We focus on quality. Each interactive whiteboard comes with features that make user interaction and content sharing easy. With our products, organizations can turn their meeting spaces into lively places that spark creativity and productivity.
Faytech’s Expertise and Experience
We have lots of experience with touchscreen technology. Faytech is a leader in interactive displays. Our advanced display technology provides excellent clarity, responsiveness, and flexibility. This knowledge helps us create products for various fields like education, healthcare, corporate settings, and retail.
We listen to our customers. We keep improving our products based on their feedback and new trends in digital collaboration tools.
Customer Support and Services
At Faytech, we care about our customers. We offer full support throughout your experience with our products. Our team helps ensure smooth user interaction by providing personalized help during setup and ongoing technical support after purchase.
We also provide resources like tutorials and best practice guides. These help users maximize engagement tools in any setting—classrooms or meeting rooms.
Get in Touch
At faytech North America, we offer innovative interactive whiteboards and educational technology solutions. Our tools help businesses and schools meet their needs. Whether you want corporate training tools or digital collaboration systems, we’re here to help. We focus on providing high-quality AV solutions that make remote learning effective and engaging.
If you want to learn more about how our products can change your workspace or classroom, please reach out to us. We know that having reliable support is important when adding new technology.
Related Topics
Get your project started with Faytech today!



